Quantum Computing and AI: Revolutionizing Application Security
In today's dynamic cybersecurity landscape, application security stands as a critical frontier. The proliferation of web applications, APIs, and interconnected systems has made securing digital assets increasingly complex.

Introduction
In today's dynamic cybersecurity landscape, application security stands as a critical frontier. The proliferation of web applications, APIs, and interconnected systems has made securing digital assets increasingly complex. While traditional security tools remain effective to some degree, they often fall short against sophisticated modern threats. Two transformative technologies—quantum computing and artificial intelligence (AI)—are poised to revolutionize application security.
🔗 Related Resource: Google Quantum AI Research
This article explores how quantum computing and AI strengthen application security through innovations like Google's Willow quantum chip and AI-driven analytical models. By combining quantum mechanics' computational power with AI's exceptional pattern recognition and decision-making capabilities, these technologies create unprecedented opportunities to detect and prevent threats in real time.
The Quantum Leap: A Primer on Quantum Computing
Quantum computing marks a fundamental shift from classical computing by leveraging quantum mechanics principles. While traditional computers use bits (0 or 1) as their basic information unit, quantum computers use qubits—which can exist in superposition, meaning they can represent both 0 and 1 simultaneously. This remarkable property enables quantum computers to process vast amounts of data in parallel, achieving exponential computational power.
🔗 Related Resource: IBM Quantum Computing
Key Features of Quantum Computing in Cybersecurity
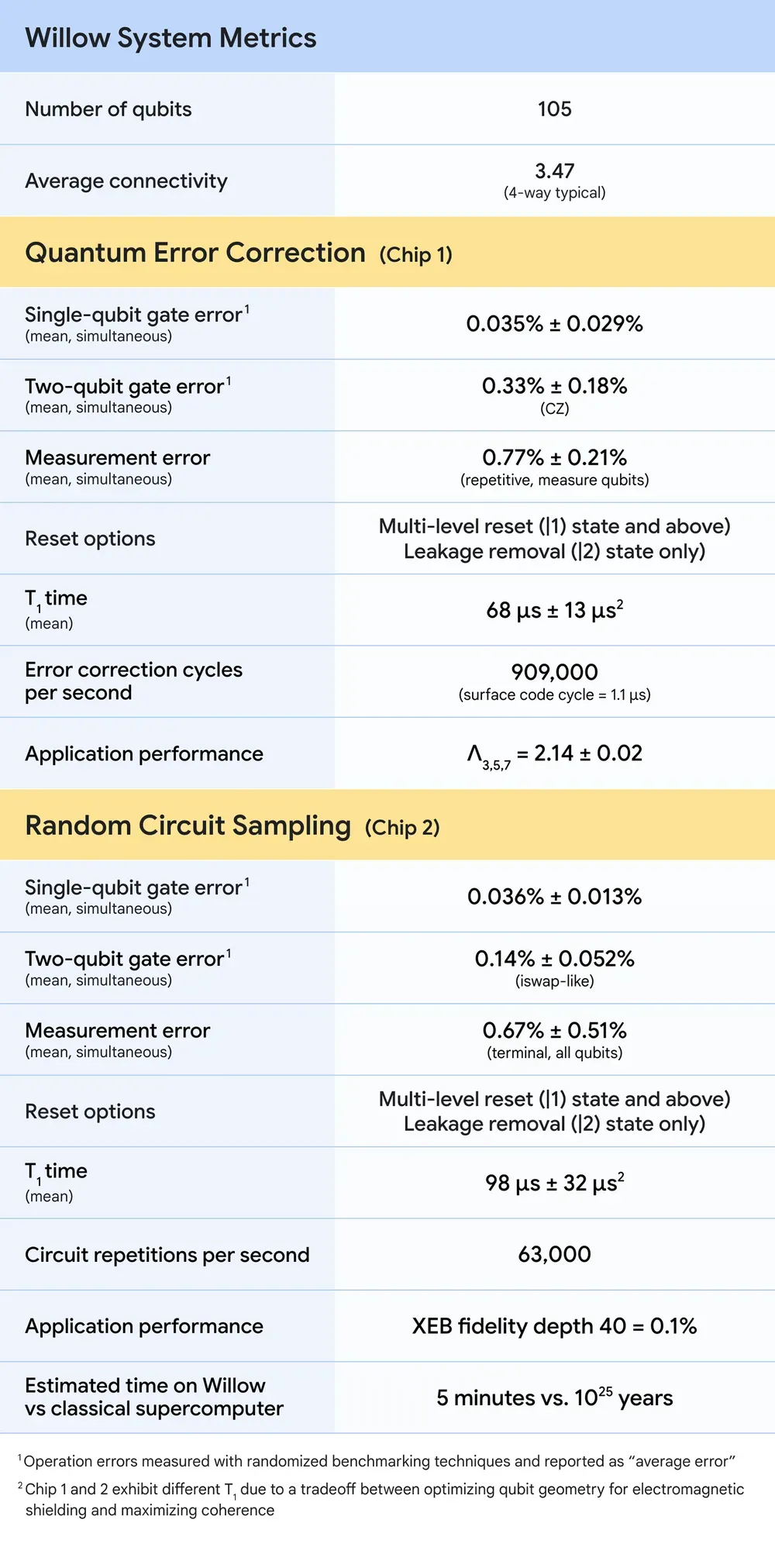
- Exponential Speedup: Quantum processors, such as Google's Willow, can solve complex problems in minutes that would take classical computers billions of years. This incredible speed proves essential for analyzing massive datasets and identifying application vulnerabilities.
- Quantum Error Correction: While errors pose a significant challenge in quantum computing, Willow's breakthrough in error rate reduction enables reliable computations, ensuring seamless execution of complex security algorithms.
- Unbreakable Encryption and Decryption: Quantum cryptography uses quantum entanglement and superposition to create theoretically unbreakable encryption protocols, protecting application data from even the most sophisticated cyber threats.
🔗 Related Resource: National Institute of Standards and Technology (NIST) Post-Quantum Cryptography
Artificial Intelligence: A Game-Changer in Security Automation
AI, with its capabilities in machine learning (ML) and deep learning (DL), has already proven to be an essential tool in application security. AI can automate threat detection, analyze patterns, and predict vulnerabilities with remarkable accuracy. When paired with quantum computing, AI can achieve levels of efficiency and accuracy previously deemed impossible.
🔗 Related Resource: Microsoft AI and Cybersecurity
AI’s Role in Application Security
- Real-Time Threat Detection: AI-powered systems can analyze network traffic and application logs to identify anomalies in real time, stopping attacks before they cause damage.
- Predictive Vulnerability Scanning: Machine learning models can predict potential vulnerabilities in application code by analyzing historical data and code patterns.
- Adaptive Defense Mechanisms: AI algorithms can dynamically adapt to evolving threats, providing a robust defense against zero-day vulnerabilities and advanced persistent threats (APTs).
🔗 Related Resource: MIT CSAIL AI Security Research
The Convergence of Quantum Computing and AI in Application Security
The combination of quantum computing and AI creates a powerful ecosystem where each technology enhances the other. Quantum computing's immense processing capabilities allow AI models to analyze vastly larger datasets and perform calculations at unprecedented speeds.
Transformative Applications
- Enhanced Cryptographic Systems: Quantum computing generates and validates cryptographic keys instantly, while AI monitors and detects system compromise attempts. Together, they ensure secure communication channels for applications.
- Advanced Vulnerability Detection: AI models powered by quantum processors can simultaneously scan millions of lines of code and network configurations, revealing vulnerabilities that traditional methods might miss.
- Secure Application Deployment: Through quantum-based simulations, developers can test and fortify applications against diverse attack scenarios before deployment.
🔗 Related Resource: Google Quantum Security Research
Case Study: Willow’s Impact on Application Security
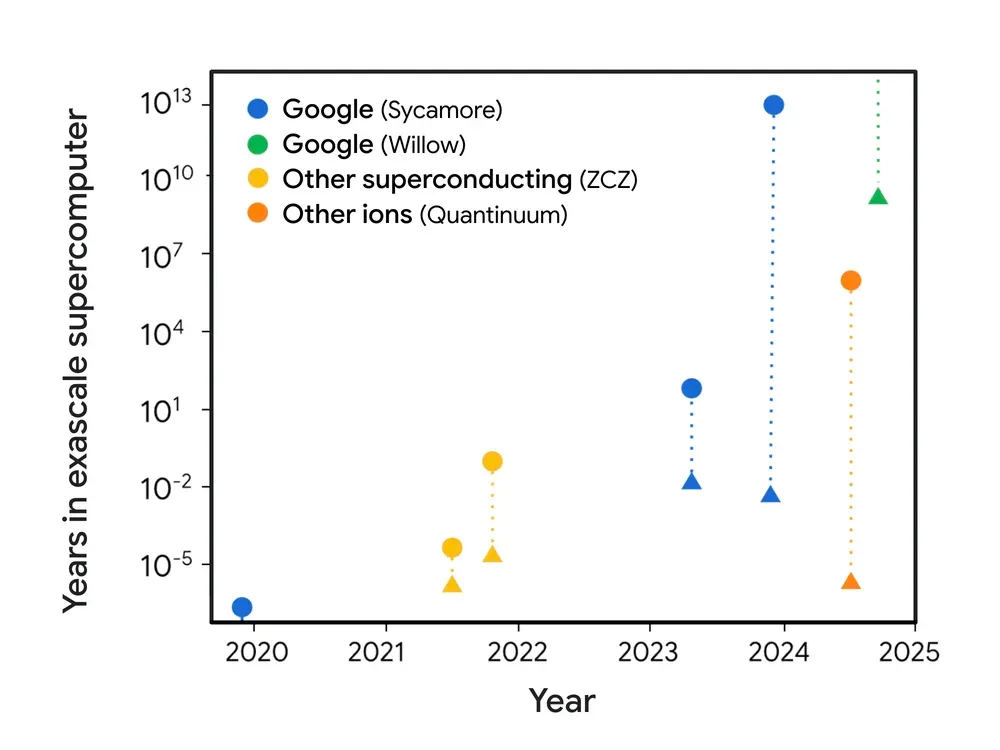
Google’s Willow quantum chip represents a significant milestone in quantum computing, demonstrating exponential error reduction and performing tasks that would take classical supercomputers 10 septillion years. In the context of application security, Willow’s capabilities translate into tangible benefits:
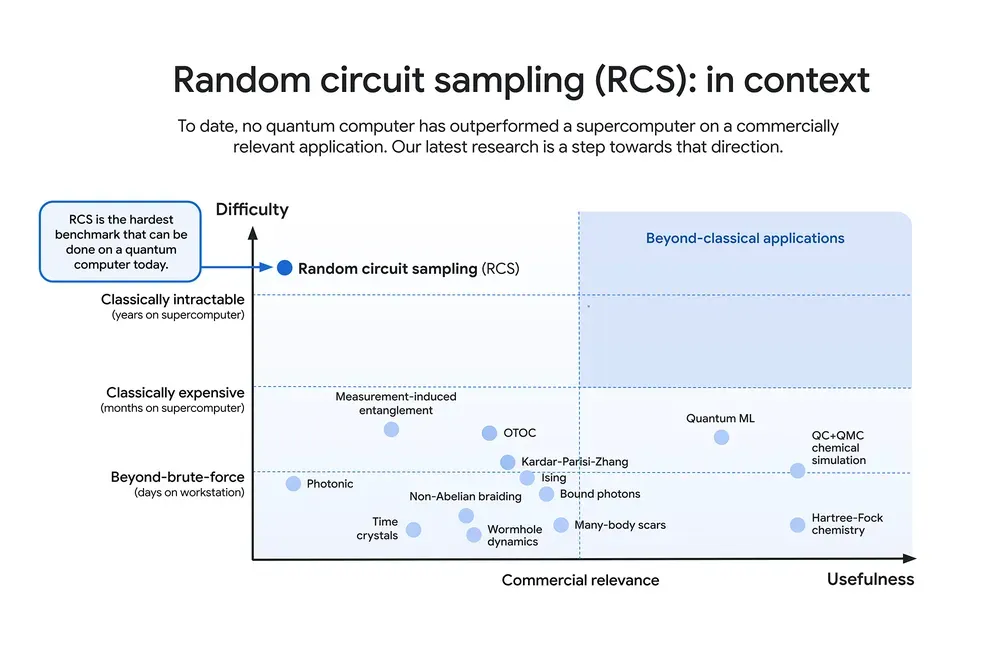
- Random Circuit Sampling (RCS) Benchmarking: Willow’s ability to perform RCS computations validates its superiority in handling tasks like cryptographic key generation and vulnerability analysis.
- Quantum Error Correction: The exponential reduction in error rates ensures that applications can rely on quantum-based security solutions without fear of computation errors undermining their integrity.
- Real-World Relevance: By achieving a beyond-classical computation standard, Willow demonstrates the potential for quantum systems to tackle real-world security challenges, from protecting sensitive user data to securing cloud-based applications.
🔗 Related Resource: Google’s Willow Quantum Chip Announcement
Resources
- Google Quantum AI Research
- IBM Quantum Computing
- National Institute of Standards and Technology (NIST) Post-Quantum Cryptography
- Microsoft AI and Cybersecurity
- MIT CSAIL AI Security Research
- Google Quantum Security Research
Conclusion: A Quantum-Driven Future for Application Security
The convergence of quantum computing and AI marks a transformative era in application security. By addressing long-standing challenges, such as quantum error correction and real-time threat detection, these technologies promise to redefine how we protect digital assets. Innovations like Google’s Willow chip serve as a testament to the potential of quantum computing to unlock new frontiers in cybersecurity.
As we stand on the cusp of this quantum revolution, the possibilities are boundless. From safeguarding sensitive data to enabling groundbreaking applications, the fusion of quantum computing and AI is set to become an indispensable pillar of modern cybersecurity. For organizations looking to stay ahead in an increasingly complex threat landscape, embracing these technologies is not just an option—it is a necessity.
🔗 Read More: Google’s Willow Quantum Chip Announcement





