Understanding API Security with OpenAPI: A Security Engineer’s Perspective
APIs are the connective tissue of modern digital ecosystems, but with great power comes great responsibility.

Introduction
As a security engineer, I’ve come to appreciate the role OpenAPI plays in shaping secure and well-documented APIs. APIs are the connective tissue of modern digital ecosystems, but with great power comes great responsibility. API security is critical, and OpenAPI provides a structured way to describe the security mechanisms protecting these APIs. It’s not just a tool for developers but also a guide for security professionals aiming to align technical implementations with security best practices. In this blog, I’ll share insights into describing API security using OpenAPI, highlight its supported security schemes, and provide practical examples that resonate with both developers and security practitioners.
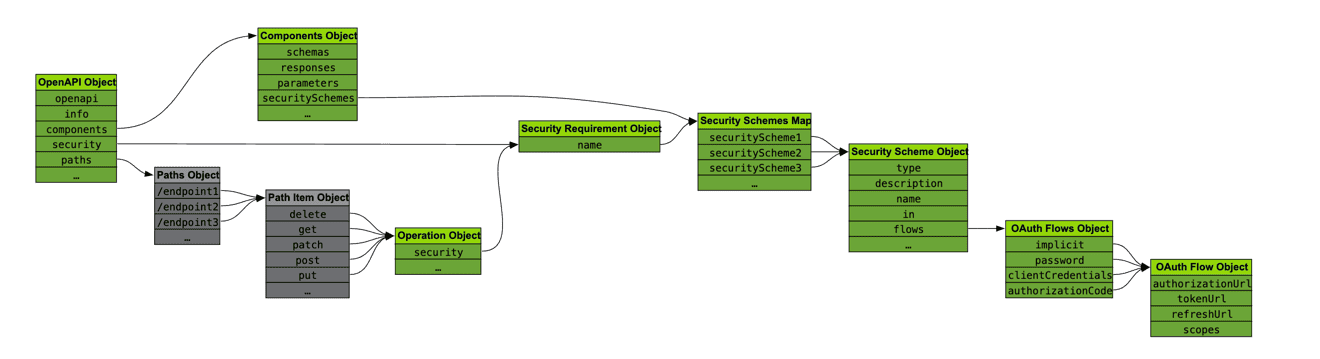
Why OpenAPI’s Security Descriptions Matter
API security often feels like balancing on a tightrope. You need to protect sensitive data without stifling usability. OpenAPI’s ability to describe security mechanisms bridges the gap between implementation and documentation. It’s like having a blueprint that helps developers, security engineers, and even tools understand how to safeguard APIs.
OpenAPI’s Security Scheme Object provides the framework to define security mechanisms, which can be referenced globally or tailored for specific operations. As someone tasked with reviewing API implementations, this clarity makes life much easier, especially when conducting security assessments or designing threat models.
The Five Pillars of API Security in OpenAPI
OpenAPI supports five key security types. Each one addresses different aspects of API protection:
- API Keys
- HTTP Authentication
- Mutual TLS (mTLS)
- OAuth 2.0
- OpenID Connect
Here’s how these apply in real-world scenarios, based on my experience.
API Keys: The First Line of Defense
API keys are often the go-to method for authenticating API requests. However, I’ve seen API keys misused or improperly secured far too many times—left exposed in code repositories or embedded in client-side applications.
Example:
components:
securitySchemes:
apiKeyAuth:
description: Use your API key to authenticate
type: apiKey
name: X-API-KEY
in: header
By clearly defining how and where API keys should be sent (in this case, via an HTTP header), OpenAPI helps prevent misconfigurations and miscommunications.
HTTP Authentication: Simplicity with Risks
Basic and Bearer authentication schemes are simple yet effective. However, they require careful implementation, especially when transmitting sensitive tokens over the network.
Example:
components:
securitySchemes:
basicAuth:
type: http
scheme: basic
bearerAuth:
type: http
scheme: bearer
bearerFormat: JWT
As a security engineer, I’d emphasize encrypting communications with HTTPS to protect these credentials in transit. The addition of bearerFormat provides clarity about token types, making integration easier for developers.
Mutual TLS: The Gold Standard
In high-stakes environments like financial services, mutual TLS is the go-to for authenticating clients. It’s not just about verifying the server—it’s about mutual trust.
Example:
components:
securitySchemes:
mutualTLS:
type: mutualTLS
Setting up mTLS requires more than just defining it in OpenAPI. It involves creating a robust PKI for certificate management. While OpenAPI doesn’t cover these deployment details, it’s an excellent starting point for documenting expectations.
OAuth 2.0: Delegated Access Done Right
OAuth 2.0 is my favorite security mechanism for APIs. It provides delegated access without exposing user credentials. However, its complexity often leads to misconfigurations, especially when defining scopes.
Example:
components:
securitySchemes:
oauth2:
type: oauth2
flows:
authorizationCode:
authorizationUrl: https://example.com/auth
tokenUrl: https://example.com/token
scopes:
read:data: Read access to data
write:data: Write access to data
By explicitly listing scopes, OpenAPI ensures that consumers and security engineers understand the boundaries of access, reducing the likelihood of privilege escalation.
OpenID Connect: Identity Beyond Authentication
OpenID Connect builds on OAuth 2.0 to provide user identity verification. It’s a must-have for applications requiring secure user authentication and authorization.
Example:
components:
securitySchemes:
openIdConnect:
type: openIdConnect
openIdConnectUrl: https://example.com/.well-known/openid-configuration
This single line simplifies integration while leveraging OpenID Connect’s dynamic discovery capabilities. It’s like plugging into a ready-made identity ecosystem.
Lessons Learned from Applying Security in OpenAPI
- Don’t Overlook Documentation
- I’ve seen APIs fail audits because their security mechanisms weren’t properly documented. OpenAPI eliminates this issue by making security descriptions part of the specification.
- Tailor Security Requirements
- Global security schemes are convenient, but operation-specific requirements provide flexibility for mixed-security environments.
- Validate Implementations
- OpenAPI descriptions are only as good as their implementation. Always test APIs against the documented security mechanisms.
A Human-Centric Approach to API Security
As security engineers, our role isn’t just about enforcing rules—it’s about enabling secure innovation. OpenAPI’s structured approach to API security helps bridge the gap between developers and security professionals. It’s not just a tool; it’s a collaboration framework. By documenting security requirements clearly, we empower developers to build securely and make security an integral part of the development process.





