Attack Surface Mapping: A Comprehensive Guide
Attack Surface Mapping (ASM) is a crucial part of cybersecurity, helping organizations identify and understand their exposure to potential threats.

Attack Surface Mapping: A Comprehensive Guide
Introduction
Attack Surface Mapping (ASM) is a crucial part of cybersecurity, helping organizations identify and understand their exposure to potential threats. With the increasing complexity of modern infrastructure, having a clear view of all accessible assets and their vulnerabilities is essential. This blog post will explore the importance of ASM, open-source tools that can be used, different methodologies, and automation techniques to keep your attack surface under control.
🔗 Related Resource: What is Attack Surface Mapping?
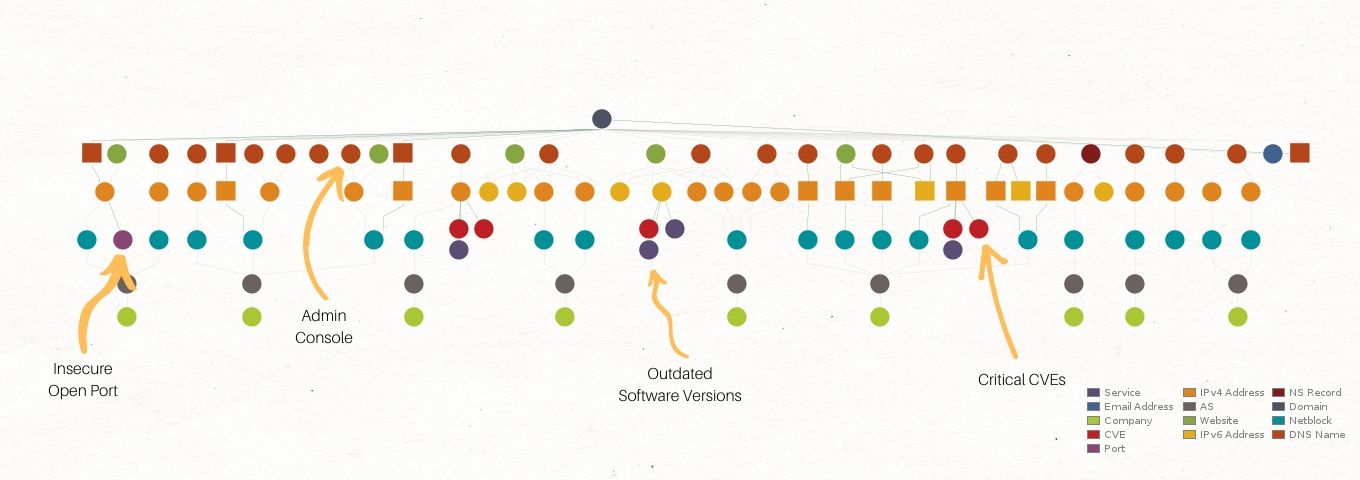
What Can Be Achieved with Attack Surface Mapping?
Attack Surface Mapping provides valuable insights into:
Open ports, running services, and technologies in use: By identifying exposed services and technologies, security teams can assess risks related to outdated software versions, misconfigurations, or unnecessary services that should be disabled.
Misconfigurations and outdated software: Many cyberattacks target systems with improper configurations or unpatched software. By mapping these vulnerabilities, organizations can prioritize patching and remediation.
Exposed API endpoints and potential data leaks: Modern applications rely heavily on APIs, and unsecured endpoints can become a gateway for attackers. ASM helps in identifying such endpoints and securing them before exploitation.
🔗 Related Resource: API Security Best Practices
Cloud asset security and misconfigurations: Cloud security is a significant concern, especially when misconfigured storage, IAM roles, or security groups expose sensitive information.
DNS and subdomain enumeration: Subdomains often lead to forgotten or unprotected assets. Enumerating them ensures that all digital assets are monitored and secured.
Third-party integrations and dependencies: Many organizations depend on external services. Understanding the security posture of third-party integrations is crucial in preventing supply chain attacks.
🔗 Related Resource: Third-Party Risk Management
Open-Source Tools for Attack Surface Mapping
1. Reconnaissance Tools
Amass: A powerful tool for passive and active DNS reconnaissance, useful for subdomain enumeration and asset discovery.
Subfinder: A fast and efficient subdomain discovery tool that leverages multiple public sources.
🔗 Related Resource: Amass Documentation
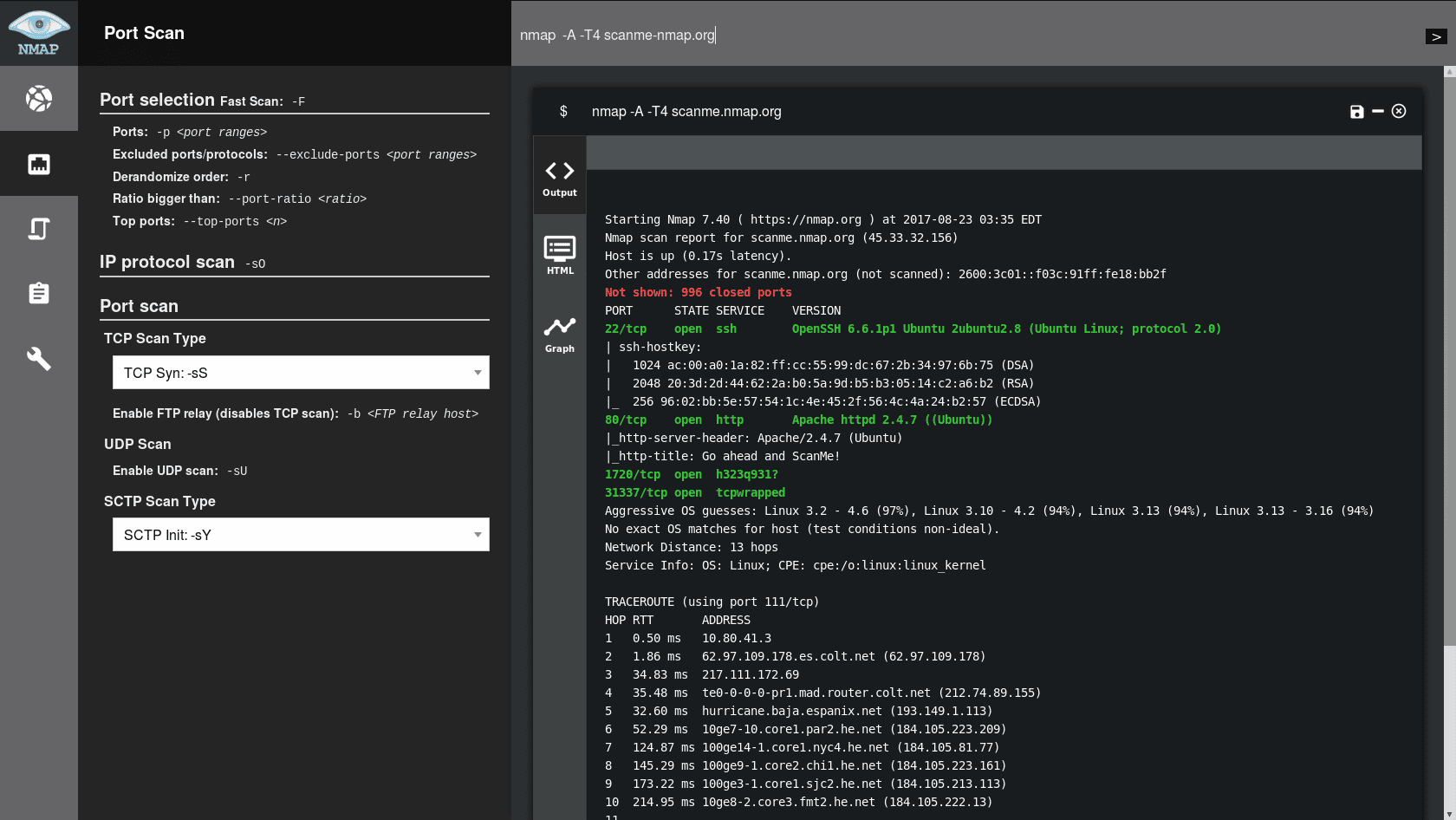
2. Port Scanning & Service Discovery
Nmap: The most widely used tool for network discovery, capable of identifying running services, their versions, and potential vulnerabilities.
🔗 Related Resource: Nmap Official Site
3. Web & API Discovery
Aquatone: Takes screenshots of discovered web interfaces, helping analysts quickly review exposed web assets.
Eyewitness: Automates web reconnaissance by capturing screenshots, collecting response headers, and extracting metadata.
🔗 Related Resource: Aquatone GitHub
4. Vulnerability Analysis Tools
Cyprox: A customizable security scanning framework that helps detect misconfigurations, security flaws, and CVEs.
🔗 Related Resource: Cyprox API Security Scanner
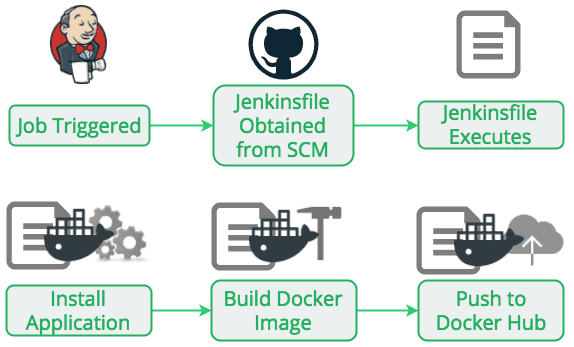
Automating Attack Surface Mapping
1. Automated Pipelines
Organizations can integrate ASM tools into CI/CD pipelines using Jenkins, GitHub Actions, or cron jobs.
🔗 Related Resource: CI/CD Security Best Practices
2. SIEM & ELK Stack Integration
ASM findings can be logged and analyzed using ELK Stack or SIEM solutions.
🔗 Related Resource: Security Information and Event Management (SIEM)
Resources
Here are some essential resources for further learning on Attack Surface Mapping:
- 🔗 OWASP Attack Surface Analysis
- 🔗 Cyprox API Security Scanner
- 🔗 Nmap Official Site
- 🔗 Cloud Security Best Practices
- 🔗 Elastic SIEM Documentation
Conclusion
Attack Surface Mapping is an essential process for securing modern digital assets. By leveraging open-source tools, organizations can identify risks before they become exploitable vulnerabilities. Continuous monitoring and automation can ensure that your attack surface remains under control.





