How DAST Teams Can Achieve ISO 27001 Compliance: A Step-by-Step Guide
DAST teams can achieve ISO 27001 compliance by conducting a gap analysis, developing an action plan, implementing aligned procedures, and committing to continuous improvement through regular audits and training, enhancing their security posture and stakeholder trust.

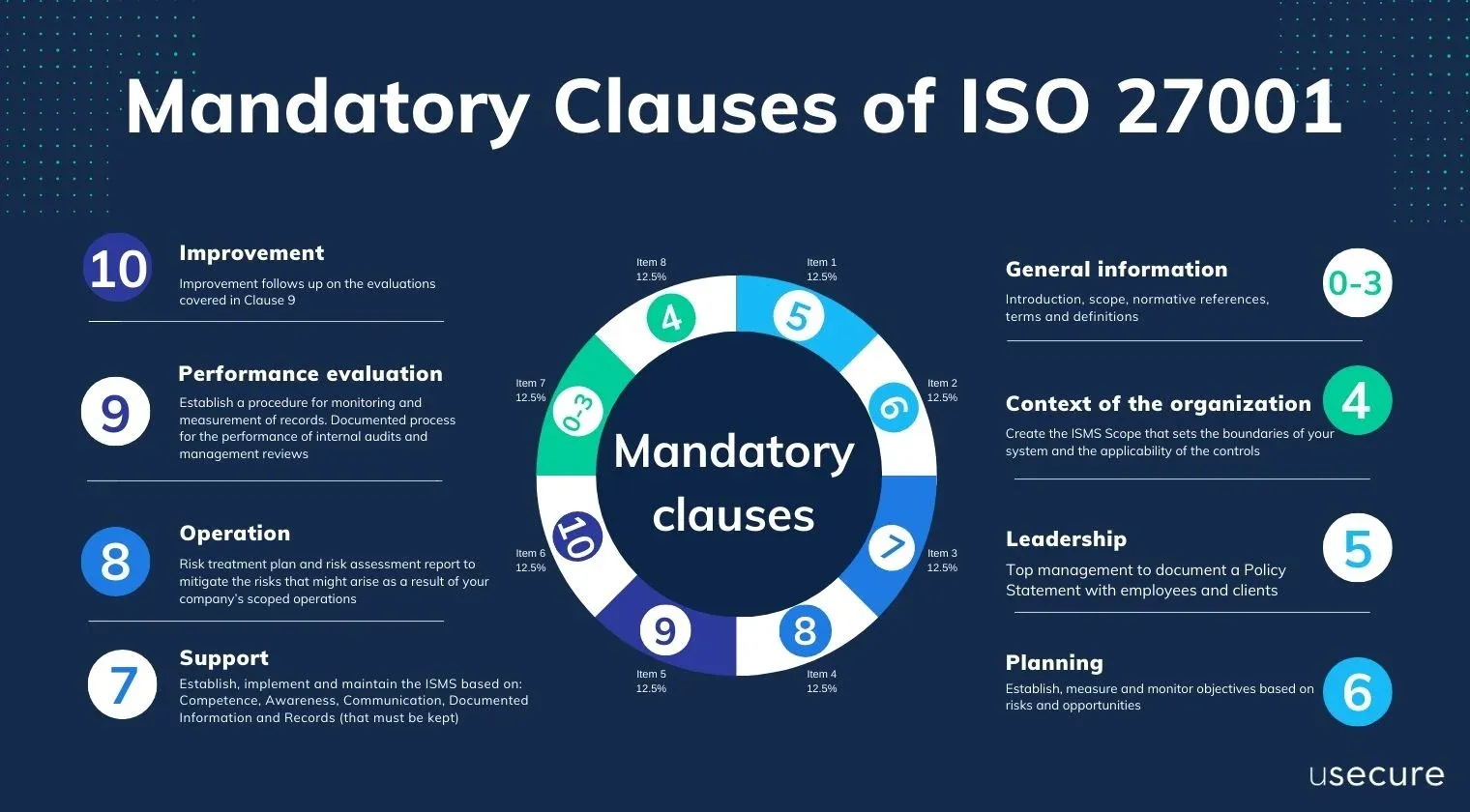
Understanding ISO 27001 and Its Importance for DAST Teams
ISO 27001 is an internationally recognized standard that specifies the requirements for establishing, implementing, maintaining, and continuously improving an Information Security Management System (ISMS). This framework is designed to help organizations manage the security of their information assets systematically.
For Dynamic Application Security Testing (DAST) teams, compliance with ISO 27001 is particularly relevant. DAST focuses on identifying vulnerabilities in running applications, and aligning these practices with ISO 27001 not only enhances security posture but also instills confidence in customers and stakeholders. By adhering to the ISO standards, DAST teams can demonstrate their commitment to protecting sensitive information, aligning security activities with organizational goals, and managing risks effectively.
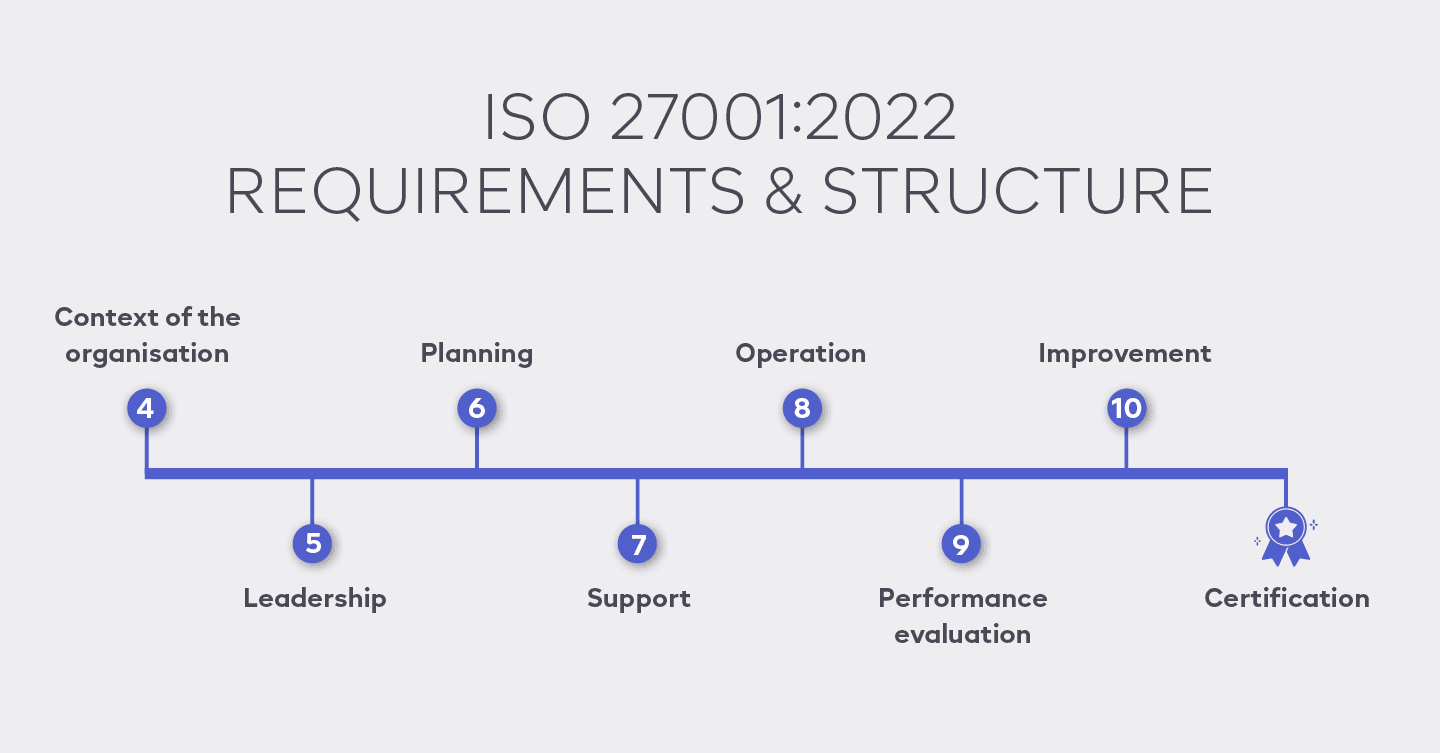
The integration of DAST within the ISO 27001 framework provides a comprehensive approach to security by ensuring that vulnerabilities are treated as part of an organization's overall risk management strategy.
Key Principles of ISO 27001 Relevant to DAST
ISO 27001 encompasses several foundational principles that are critical for DAST teams to understand and implement:
-
Risk Management: At the heart of ISO 27001 is the concept of risk management. DAST teams must assess application vulnerabilities as part of a broader risk assessment to determine which risks are acceptable and how vulnerabilities should be mitigated. For more on risk management, check out our article on cybersecurity vulnerabilities.
-
Continuous Improvement: ISO 27001 emphasizes the importance of ongoing monitoring and continual improvement of the ISMS. DAST practices should therefore be regularly evaluated and refined to adapt to evolving threats. Explore our blog on attack surface mapping to learn more about maintaining security.
-
Documentation and Control: ISO 27001 requires organizations to document their security policies, processes, and controls. DAST teams need to maintain thorough records of testing methodologies, findings, and remediation steps to meet compliance.
-
Integration with Security Policies: DAST practices must align with an organization's overarching security policies. Ensuring coherence between security initiatives and regulatory requirements is vital for effective compliance.
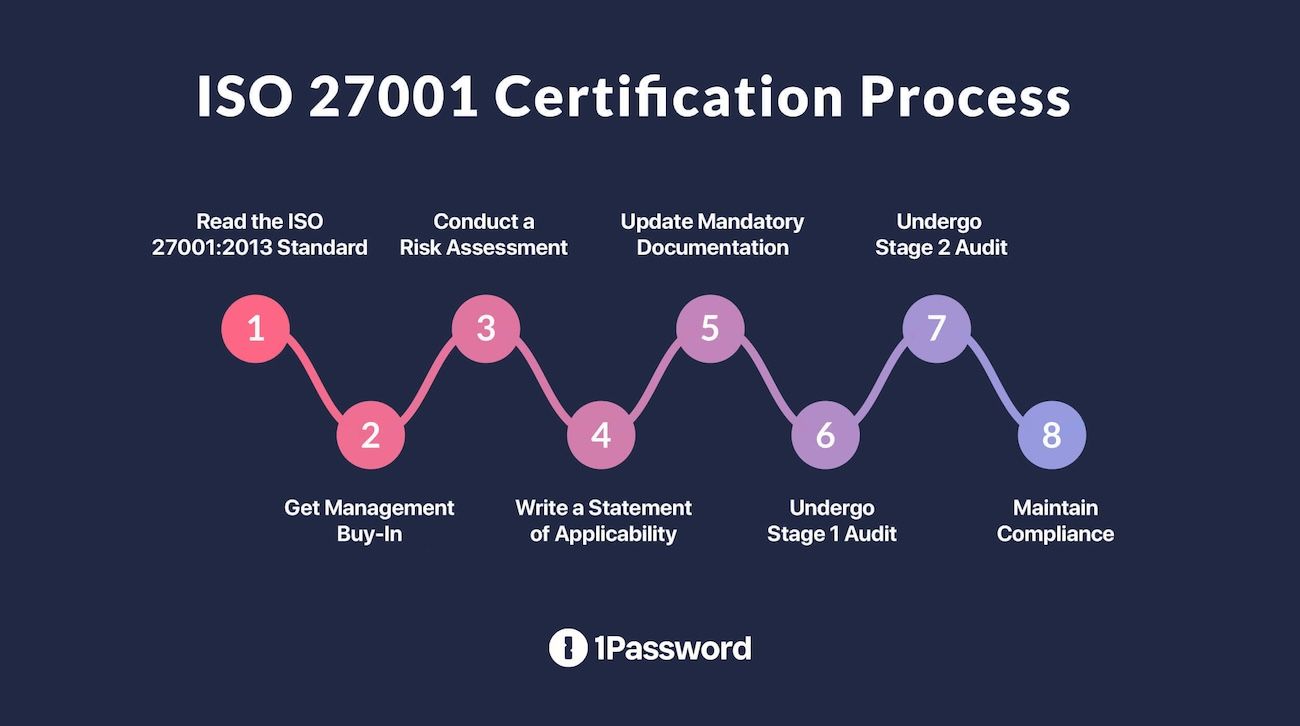
Step 1: Conducting a Gap Analysis for DAST Practices
The first step in achieving ISO 27001 compliance is to conduct a comprehensive gap analysis of current DAST practices against the standard's requirements. This analysis involves assessing existing processes, tools, documentation, and overall effectiveness in addressing security vulnerabilities.
Checklist for Gap Analysis:
- Review existing DAST methodologies and tools alignment with ISO 27001 clauses.
- Evaluate documentation practices to ensure they meet ISO requirements.
- Assess stakeholder involvement and clarity in roles related to information security.
- Identify training needs for team members regarding ISO 27001 standards.
Common pitfalls that DAST teams encounter during this evaluation include a lack of clear documentation and insufficient integration with other security processes. Engaging stakeholders across security, development, and compliance teams can mitigate these issues and foster a collaborative approach.
Step 2: Developing an Action Plan for Compliance
Once the gap analysis is complete, the next step is to create a detailed action plan outlining how the DAST team will address identified gaps. This plan should encompass:
- Timelines: Set realistic deadlines for implementing changes and achieving compliance.
- Responsibilities: Clearly define roles and responsibilities within the team for each task.
- Resource Allocation: Identify the resources required for training, tool enhancements, and process improvements.
Make sure to include methodologies for addressing the identified gaps, such as workshops for security awareness training or hiring a consultant for expertise in ISO 27001 compliance. Setting measurable goals will help track progress and motivate the team to achieve compliance.
Step 3: Implementing DAST Procedures Aligned with ISO 27001
With a structured action plan in place, DAST teams can begin to implement procedures that align with ISO 27001 requirements. Here are some best practices for this process:
-
Integrate DAST into CI/CD Pipelines: Ensure that DAST is part of the continuous integration and continuous deployment processes. This inclusion guarantees that testing occurs regularly and vulnerabilities are identified early in the development lifecycle.
-
Document DAST Processes: Maintain thorough documentation of DAST methodologies, testing protocols, and incident response procedures. This documentation should reflect the requirements set forth by ISO 27001.
-
Select Appropriate Tools: Implement tools that aid in DAST activities while ensuring they adhere to ISO standards. Automation tools can facilitate consistent testing and reporting, making compliance more manageable. Learn more about integrating AI in application security through our blog on AI in API Security.
Maintaining ISO 27001 Compliance and Continuous Improvement
Achieving ISO 27001 compliance is not a one-time effort; it requires ongoing commitment. DAST teams should establish a regular schedule for compliance reviews and updates to their processes. Here are some strategies to maintain compliance:
- Conduct Periodic Audits: Regular audits help ensure that DAST prand motivate the team to achieve compliance.
Step 3: Implementing DAST Procedures Aligned with ISO 27001
With a structured action plan in place, DAST teams can begin to implement procedures that align with ISO 27001 requirements. Here are some best practices for this process:
-
Integrate DAST into CI/CD Pipelines: Ensure that DAST is part of the continuous integration and continuous deployment processes. This inclusion guarantees that testing occurs regularly and vulnerabilities are identified early in the development lifecycle.
-
Document DAST Processes: Maintain thorough documentation of DAST methodologies, testing protocols, and incident response procedures. This documentation should reflect the requirements set forth by ISO 27001.
-
Select Appropriate Tools: Implement tools that aid in DAST activities while ensuring they adhere to ISO standards. Automation tools can facilitate consistent testing and reporting, making compliance more manageable. Learn more about integrating AI in application security through our blog on AI in API Security.
Maintaining ISO 27001 Compliance and Continuous Improvement
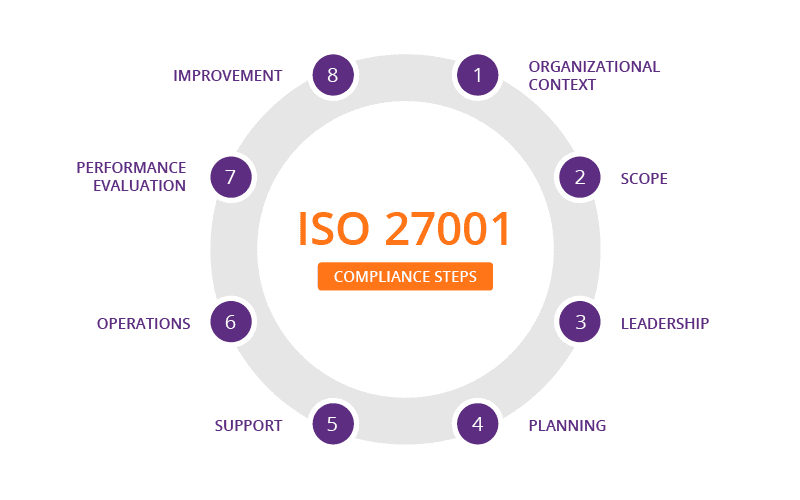
Achieving ISO 27001 compliance is not a one-time effort; it requires ongoing commitment. DAST teams should establish a regular schedule for compliance reviews and updates to their processes. Here are some strategies to maintain compliance:
-
Conduct Periodic Audits: Regular audits help ensure that DAST processes remain aligned with ISO 27001 standards. These audits provide critical insights into areas for improvement and allow for proactive response to any compliance gaps.
-
Automate Reporting and Documentation: Automating the reporting process can help ensure that comprehensive records are maintained effortlessly, thereby aiding compliance efforts.
-
Training and Awareness: Regular training sessions and updates on ISO standards keep team members informed of best practices and evolving security landscapes. Continuous professional development is essential for adapting to new threats.
-
Leverage Audit Results: Use findings from audits to drive improvements within the DAST team’s practices. Establish feedback loops to continuously refine procedures and enhance security measures.
Conclusion
Achieving ISO 27001 compliance is essential for DAST teams striving to enhance their security practices and protect critical information assets. By following the outlined steps—conducting a gap analysis, developing an action plan, implementing robust DAST procedures, and committing to ongoing compliance—teams can align their dynamic application security testing efforts with established international standards. This alignment not only fortifies their security posture but also cultivates trust among stakeholders and customers alike.
Resources
- ISO 27001 Overview - International Organization for Standardization
- NIST Special Publication on Information Security - National Institute of Standards and Technology
- OWASP Top Ten API Security Risks - Open Web Application Security Project
- MITRE ATT&CK Framework - Comprehensive resource for understanding adversary tactics and techniques
- Cybersecurity Framework - NIST Cybersecurity Framework for managing cybersecurity risk
- ISO 27001 Compliance Checklist - A detailed checklist for ISO 27001 compliance.
- OWASP Application Security Verification Standard (ASVS) - Framework for defining security requirements.
- Understanding the OWASP API Security Top 10 - A closer look at common API vulnerabilities.
- Understanding API Security with OpenAPI: A Security Engineer Perspective - Insights on API security practices.





